INPROA HST PREVENTS 100% OF HACKING ATTACKS BY SIMPLY HIDING YOUR DATA OFFLINE
Inproa Hidden Sovereign Technology has a proactive stance on security. Your confidential data is stored offline and never connected to the internet, so it cannot be targeted or leaked. In our system, you have two working environments. One online for daily internet- related tasks and one fully secure offline environment for confidential information.
Security By The Numbers
In 2023 half of all small businesses were hacked. Hacking and data breaches will be the new norm for companies going forward, and the monetary loss is staggering:
DATA
BREACHES
2019: 8 billion records stolen
2023: over 60% of Organizations Experienced
RANSOMWARE
ATTACKS
2019: 188 million attacks
2023: over 60% of Organizations Experienced
2020: Covid-19 And Remote Work

When the majority of the world is working from home vulnerabilities emerge. Phishing emails, malware, ransomware, and all variations of cyber crimes have increased drastically.
Due to remote work
of businesses is expected to experience a data breach.
April: Google Blocked
daily malware and phishing emails related to Covid-19.
May: An increase of
in cyber attacks against banks are linked to Covid-19.
May: The FBI reported at
increase in the number of reported cybercrimes.
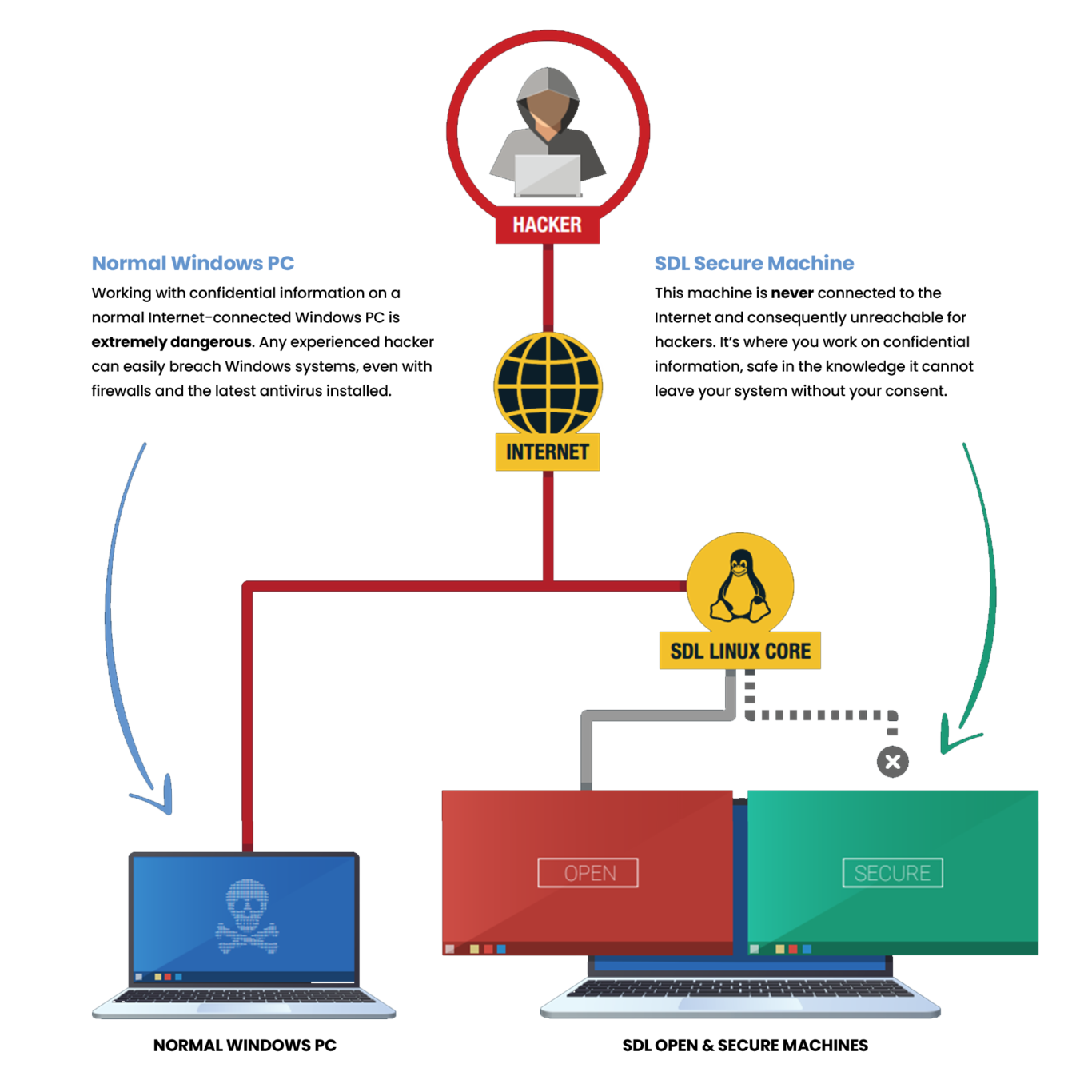
No Internet, No HACKERS
You can’t hack what you can’t see. A hacker uses the internet to gain access to the victim’s computer, and if that computer is not connected to the Internet it’s invisible to the hacker. With Inproa SDL you store your confidential data offline in our Secure Machine, and use the internet on our Open Machine. It’s like having two computers in one PC.
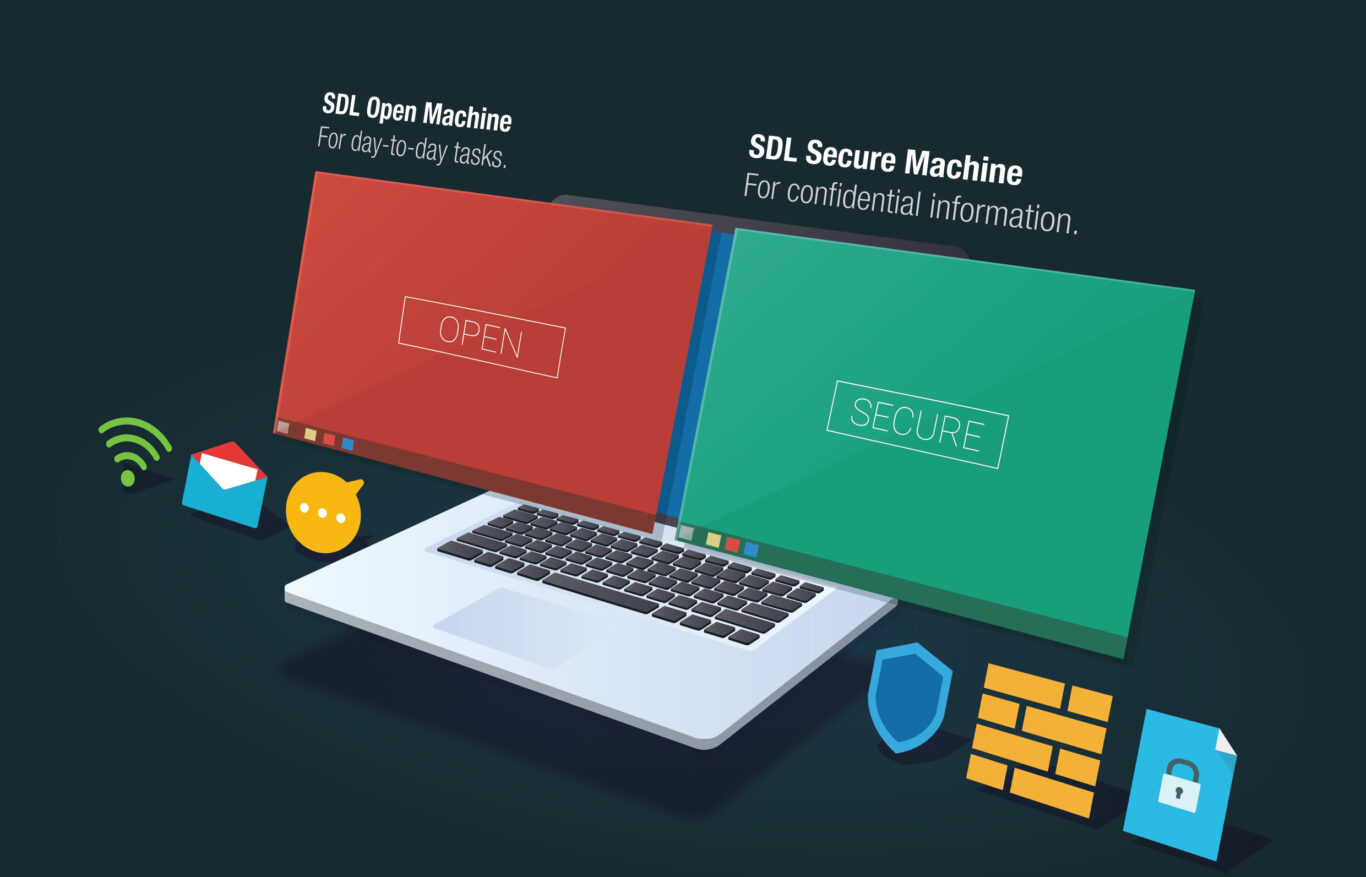
Two Computers In One PC
Turn your computer into a fortress. Inproa SDL utilizes the power of Linux and virtualization to create a dual working environment. One for day-to-day internet-related tasks and one fully secure environment that has no Internet connection. The user quickly switches between these two environments at the push of a button.
DON’T PANIC, RESTORE
Completely remove viruses, trojans, and other malware. If your computer gets infected, you can easily remove the malware with our unique Restore-function. It’s the only 100% effective solution for completely removing malicious code from your system.

WHAT IS RESTORE?
Since the Open and Secure Machines are both running in a
virtualized environment controlled by our SDL Linux core,
they can both be backed up on a system level. This means
your entire operating system is backed up and can be
restored in its entirety, completely removing any infection.
Virtualized Backup and Restore
- Complete low-level OS backup
- Much faster than traditional backups
- Restore in 10-seconds
- Resets the entire system
- Removes all infections
Restore works for:
NO INFECTED USB-DEVICES
Where has this USB-device been before? USB sticks are a convenient way to move files between computers, and it’s also a convenient way for malware to spread. With Inproa SDL you can only use USB devices registered with your system; an unknown device won´t be recognized. This prevents the risk of accidental infection of your system.

The USB Manager
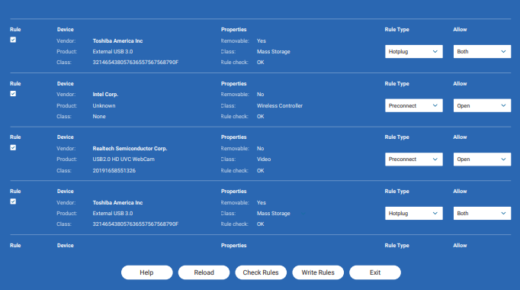
In our USB manager, you can grant access to the USB devises you want to use. Either give the device access to the Open or Secure Machine, or both Machines. From here you can also disable internal USB devices like your laptops built-in camera.
WHAT MAKES SDL SO SECURE?
Where has this USB-device been before? USB sticks are a convenient way to move files between computers, and it’s also a convenient way for malware to spread. With Inproa SDL you can only use USB devices registered with your system; an unknown device won´t be recognized. This prevents the risk of accidental infection of your system.
Simple Design Minimal Attack Surface Secure Platform Proactive rather

Latest New Form Blog
Stay updated with the latest news and articles from Inproa




